Wondering how an e Sign can help your business prevent frauds? Yes, when your e Sign online through Protean eGov Technologies’ e Sign Pro, you can add a strong shield to your business’s identity verification process.
In this digital age, a majority of contracts are executed online, offering speed and convenience. However, this shift has also amplified the risk of identity fraud. Identity fraud can be seen as a major threat that many businesses continue to underestimate.
Fraudsters can impersonate legitimate parties, forge signatures, and create binding obligations that expose organisations to serious consequences such as:
- Financial losses
- Legal disputes
- Reputational harm
For regulated sectors such as financial services and capital markets, even minor lapses in identity verification can cause action from regulators like RBI, SEBI, or PFRDA. This makes reliance on weak or unsecured signature methods a significant and often overlooked risk in contractual processes.
The Flaws of Traditional and Simple e Signatures
Paper-based signatures can reduce the speed of verification because they require in-person verification. This can make them impractical for remote or international contracts.
Basic e Sign methods like scanned images, inserted signatures, or simple click-to-sign methods may seem convenient. However, they fail to properly verify the signer’s identity. These methods can also be easily misused. Physical signatures can have the risk of being copied, reused, or attached to altered documents, creating opportunities for fraud.
Moreover, physical signatures can be difficult to verify and may provide weaker legal proof compared to digitally verified electronic signatures with robust audit trails.
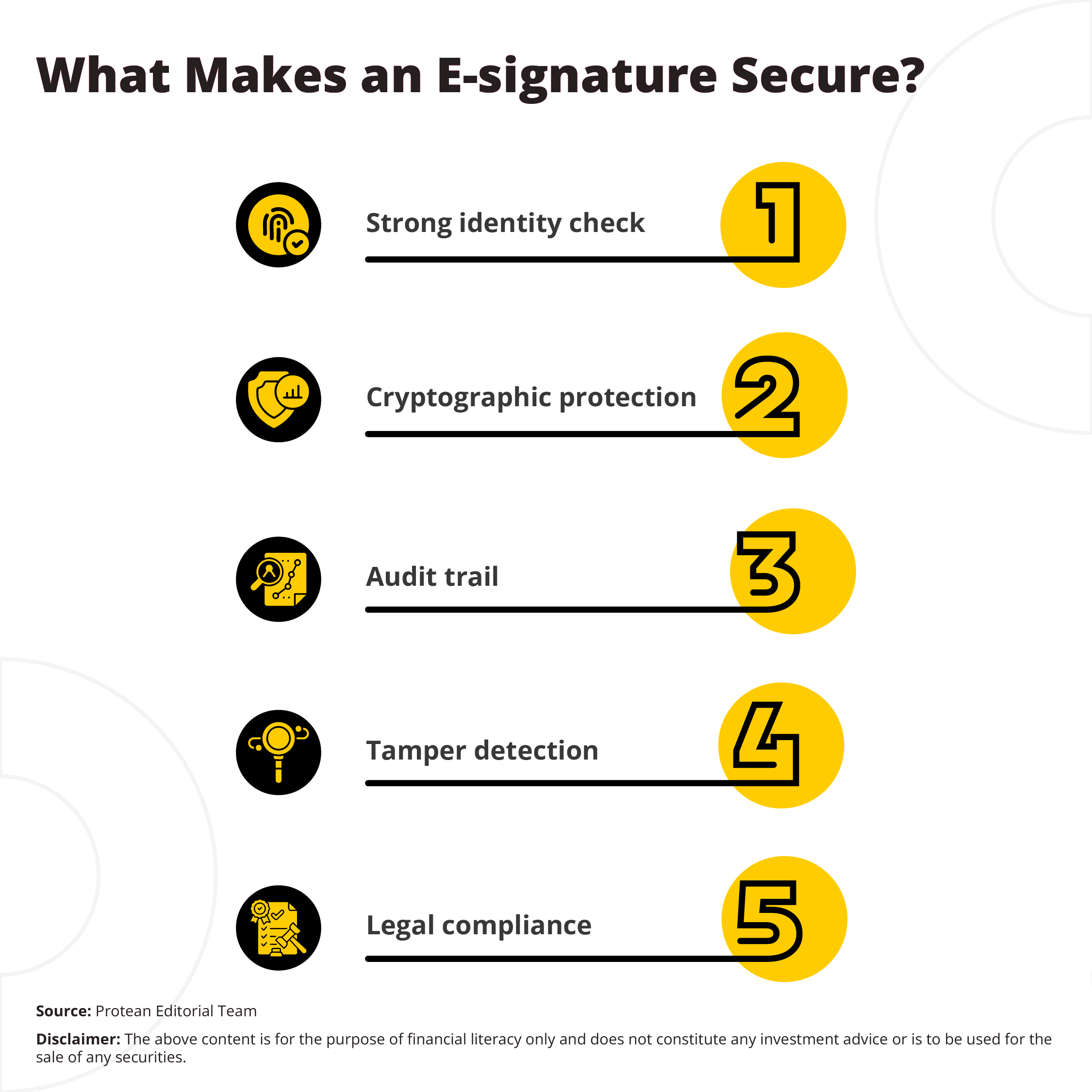
What Makes an E-signature Secure?
The following features can make an e Sign online more secure with e Sign Pro:
Strong identity check
The beneficiary’s identity needs to be verified through Aadhaar OTP/biometric, KYC, or two-factor authentication. In India, Aadhaar eSign links the signature directly to the person’s Aadhaar ID.
Cryptographic protection
Using Public Key Infrastructure (PKI), the e Sign is locked to the document. If the document is changed, the e Sign online in the document would become invalid.
Audit trail
A secure system can record details like time, device, IP address, and steps taken during signing. This log can be used as proof in case of disputes.
Tamper detection
If anyone tries to edit the contract after signing, the eSign Pro system will show that the document has been changed.
Legal compliance
The e-signature must follow the IT Act, 2000 and CCA rules. In India, a valid e-signature is treated the same as a handwritten one.
How a Secure e Sign Online Solution Can Prevent Fraud
Here is how a secure e Sign online process can help in preventing fraud:
- Identity proof upfront – The system would verify the beneficiary’s identity using Aadhaar OTP, biometric checks, KYC, or government IDs. With this, it can block impersonation from the start.
- Multi-factor / risk-based checks – As per regulatory guidelines, and depending on transaction risk, the system can add extra checks like device fingerprinting, alternate OTPs, or facial recognition.
- Binding cryptographic signature – A digital certificate issued by a licensed Certifying Authority like e Sign Pro would bind the e Sign to the document, making tampering invalid.
- Audit and logging – Every action during signing is captured in a tamper-proof log, providing strong evidence in case of disputes.
- Certificate verification – The system can confirm that the beneficiary’s certificate truly belongs to them, preventing misuse of someone else’s credentials.
- Tamper alerts and sealed documents – Once signed, the document is sealed, and any attempt to alter it would either break the seal or trigger an alert.
- Real-time anomaly detection – Advanced systems like e Sign Pro use machine learning to spot unusual behavior. Examples of unusual behavior are signings from odd locations or repeated failures.
- Legal enforceability – Signed documents are legally valid and enforceable, since the process complies with the IT Act, CCA rules, and SEBI-recognised practices.
Key Security Features of E Sign Pro to Look For
When selecting an e Sign Pro service, you can ensure it is offering the following features:
- Strong identity verification (Aadhaar OTP/biometric, government ID, KYC)
- PKI-based digital signature issuance via a licensed Certifying Authority
- Comprehensive audit trail capturing timestamps, IP, device, user actions
- Tamper detection / sealed document enforcement
- Certificate verification / binding to identity (no misuse of someone else’s credential)
- Risk-based authentication and multi-factor options
- Anomaly detection / fraud analytics
- Legal compliance and standards certification (CCA, IT Act, records retention)
These features can distinguish a truly secure offering (e Sign Pro) from a basic eSign.
Conclusion
A well-designed e Sign Online with Protean eGov Technologies’ e Sign Pro solution can integrate:
- Strong identity checks
- Cryptographic protection
- Detailed audit trail
- Tamper detection
- Real-time fraud monitoring
Choosing a secure e Sign solution is therefore not just about business convenience. It is a proactive step to protect contracts from fraud and ensure that every signature carries full legal enforceability. Go ahead and request for a demo now.
Frequently Asked Questions (FAQs)
Is an e Sign legally valid in India?
Yes. Under the Information Technology Act, 2000, an electronic signature executed in the prescribed manner is equivalent to a handwritten signature (Section 5). Contracts formed electronically are also valid under Section 10A.
Can SEBI-regulated entities use e Sign?
Yes. SEBI has issued informal guidance wherein, for certain disclosures (like client fee schedules), an electronic signature under compliant methods is acceptable.
Does Aadhaar eSign prevent all fraud?
No technology can guarantee zero fraud. However, Aadhaar e Sign can strengthen identity verification by linking signatures to UIDAI-verified identities. Coupled with device checks, audit logs, and anomaly detection, it forms a strong deterrent.
What happens if a signed document is altered after signing?
In a secure system, tampering invalidates the cryptographic seal or triggers alerts. Versioning is preserved and the original signature no longer verifies.
Are there regulatory trends emphasising stronger authentication?
Yes. The RBI’s upcoming guidelines require risk-based authentication and stronger multi-factor controls for digital transactions. These trends push enterprises to adopt stronger identity safeguards in all digital workflows.