In India’s digital economy, seamless identity verification is critical for ensuring trust, preventing fraud, and expanding financial inclusion. Aadhaar authentication plays a central role in enabling these outcomes. For businesses, especially in fintech, banking, telecom, and e-governance, etc., understanding the implications of Aadhaar authentication is essential for delivering secure and compliant customer experiences.
What is Aadhaar Authentication?
Aadhaar authentication is a real-time, online process where the Aadhaar number and other data such as demographic or biometrics submitted by a user are matched with records in the Central Identities Data Repository (CIDR), managed by the Unique Identification Authority of India (UIDAI). Its objective is to authenticate the individual’s identity with 'Yes' or 'No' response from UIDAI, thereby confirming the user’s authenticity.
The key stakeholders in this ecosystem include:
- UIDAI, which manages Aadhaar infrastructure and sets guidelines.
- Authentication User Agencies (AUAs), entities like banks and telecoms that use authentication services.
- KYC User Agencies (KUAs), which are permitted to conduct Aadhaar-based KYC using eKYC APIs.
The authentication flow typically follows this path:
- The user shares an Aadhaar number and a specific authentication factor (e.g., fingerprint, OTP).
- The AUA/KUA sends this data securely to UIDAI.
- UIDAI matches it with CIDR records and responds with a binary confirmation.
This framework supports efficient service delivery, streamlines onboarding, and strengthens compliance, all while protecting user identity and data.
Pillars of Aadhaar Authentication
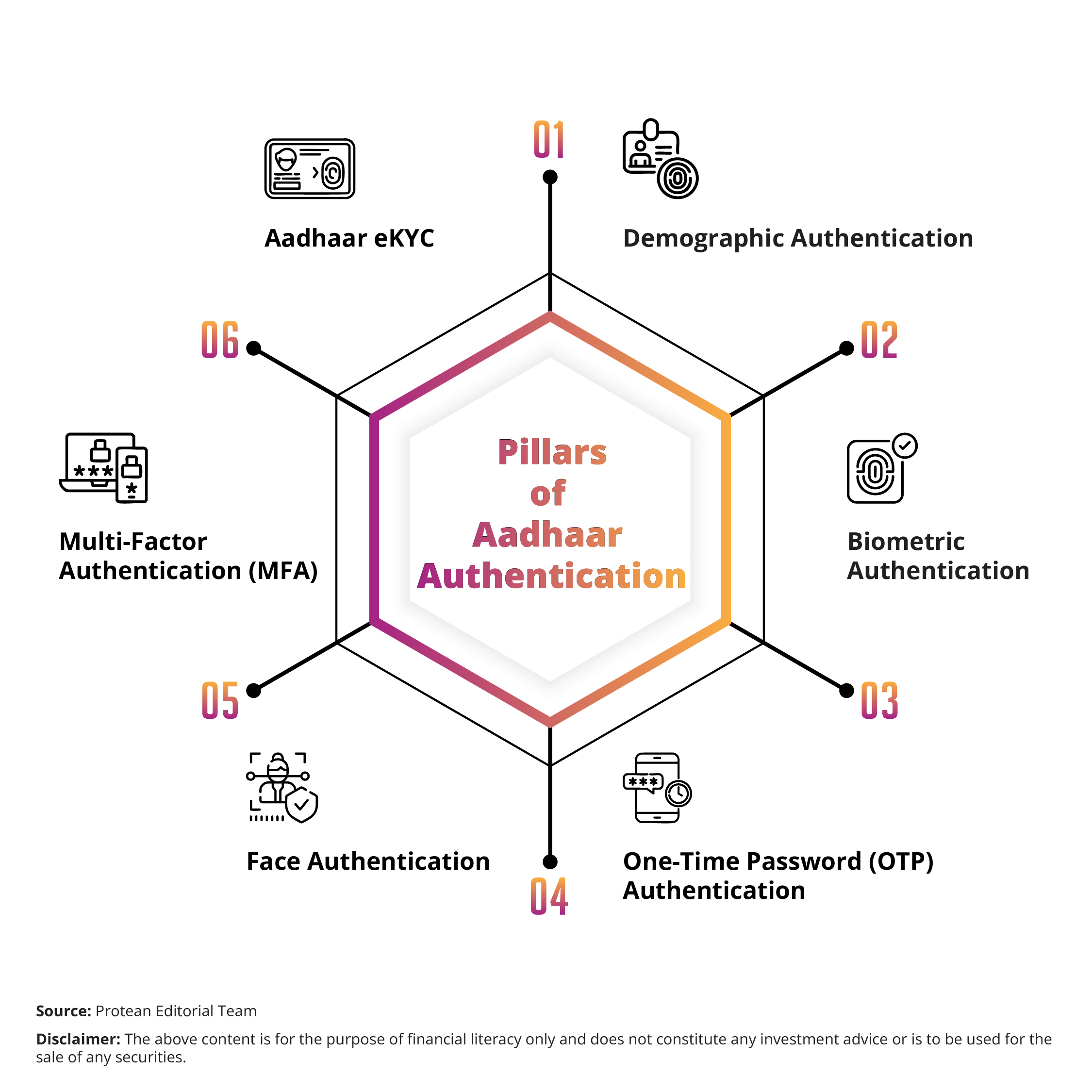
Aadhaar authentication can be implemented through multiple methods, each suited to different business use cases and user access channels. These can include the following:
1. Demographic Authentication
This is the most basic form of Aadhaar authentication. Here, you can validate user details such as name, date of birth, gender, and address against the information stored in the CIDR.
It is often used in non-sensitive environments where biometric or OTP may not be feasible, such as large-scale surveys or low-risk subsidy verifications.
2. Biometric Authentication
Biometric authentication uses either fingerprints or iris scans. The biometric data is encrypted and sent securely to the CIDR for matching.
It is widely used by banks, NBFCs, and public distribution systems for high-trust transactions such as cash withdrawals, account access, and direct benefit transfers (DBTs).
As reported by IBEF, UIDAI processed over 150 billion Aadhaar Authentication transactions till May 2025, demonstrating its rising reliability and enterprise adoption.
Learn more about the benefits of Aadhaar authentication here.
3. One-Time Password (OTP) Authentication
This method sends an OTP to the user’s registered mobile number or email linked with Aadhaar. The user inputs this OTP to verify identity.
It is suitable for low-friction digital interfaces, such as e-commerce platforms, telecom customer verifications, and fintech onboarding processes.
4. Face Authentication
Introduced by UIDAI in 2018, face authentication method uses facial recognition technology, matched with the photograph stored in Aadhaar.
5. Multi-Factor Authentication (MFA)
MFA combines two or more authentication types which may be demographic and OTP or biometric and OTP, for a higher level of security and assurance.
6. Aadhaar eKYC
While not a standalone authentication mode, Aadhaar e-KYC leverages the authentication framework to provide verified demographic data to KUAs.
There are two main types:
- Online eKYC (with user consent): Provides demographic data and photograph directly from UIDAI to the requesting entity.
- Offline eKYC (XML/PDF-based): Allows Aadhaar holders to download their details and share it manually.
eKYC has revolutionised digital onboarding across sectors such as mutual funds, insurance, and telecom.
The government has permitted private entities to access Aadhaar authentication services.
The Reliability and Security Framework of Aadhaar Authentication
The UIDAI operates under a strict framework designed to ensure data integrity, user privacy, and cybersecurity. This includes:
- End-to-End Encryption: All Aadhaar authentication requests are encrypted, both in transit and at rest, using prescribed standards.
- Consent-Based Architecture: Every authentication is performed only after obtaining informed and explicit consent from the Aadhaar holder.
- Tamper-Proof Audit Trails: Every request and response are logged to create a non-repudiable record, ensuring transparency and traceability.
- UIDAI Oversight: The UIDAI regulates AUAs and KUAs, with penalties for misuse and regular audits for compliance.
Conclusion
As India deepens its digital infrastructure and services, Aadhaar authentication remains a foundational pillar for identity assurance. Its evolving types viz., biometric to OTP to facial recognition, enable flexibility and inclusivity, while safeguarding security and privacy.
For enterprises seeking to operate in India’s digital space, understanding the types of Aadhaar authentication is not merely a technical necessity rather it is a strategic advantage. Whether you are a fintech building seamless onboarding journeys, a bank strengthening KYC compliance, or a government agency delivering benefits at scale, Aadhaar authentication offers a secure, scalable, and regulatory-aligned path forward.
Protean has been at the forefront of digital transformation in India, and its Aadhaar Authentication APIs bring enterprise-grade security and simplicity to identity verification.