Before discussing Aadhaar authentication, it is important to note that since its inception, Aadhaar has become the base of India's digital identity infrastructure. Over 1.3 billion Aadhaar numbers have been issued by the Unique Identification Authority of India (UIDAI), empowering seamless access to banking, telecom, subsidy disbursals, and digital services.
The Aadhaar-based authentication system enables residents to verify their identity digitally and securely across both public and private sector ecosystems.
However, given its widespread utility, a critical question emerges: How secure is Aadhaar authentication? Let us learn more about how secure Aadhaar authentication is.
Security Architecture of Aadhaar
UIDAI’s Aadhaar authentication system is underpinned by a multi-layered security architecture that protects data at every point, from enrollment to storage, transmission, and usage.
Read about how Aadhaar authentication is transforming different sectors.
1. Security of the Central Identities Data Repository (CIDR)
At the core of the Aadhaar infrastructure lies the CIDR, which securely houses biometric and demographic information. The CIDR is safeguarded through advanced security measures, including 256-bit encryption, robust firewalls, stringent access controls, and continuous surveillance. The UIDAI ensures that no third-party entity is granted direct access to this core database.
Furthermore, the UIDAI functions within a zero trust architecture, where every component, whether internal or external, must undergo independent authentication and authorisation. This security framework is further strengthened through comprehensive access logs, detailed audit trails, and stringent physical security measures at data centers.
2. Data Protection in Transit and at Rest
To ensure end-to-end confidentiality, all Aadhaar-related data is encrypted using AES-256 during both transmission and storage. UIDAI mandates the use of Public Key Infrastructure (PKI) for all requests made to the authentication server. Even when a request travels from a bank or a telecom operator to UIDAI, the data packet remains encrypted and tamper-proof.
Entities such as Authentication User Agencies (AUAs) and KYC User Agencies (KUAs) are licensed and regulated by UIDAI. They are subject to stringent audits, and any breach of protocol can result in penalties or blacklisting.
3. Biometric Security and Anonymisation
Biometric data (fingerprints, iris scans, and face templates) are never stored or shared by user-facing agencies. The system is designed to transmit only hashed values, ensuring that original biometric data cannot be reconstructed. Additionally, UIDAI implements data minimisation principles: only essential identity markers are used during authentication, significantly reducing exposure risks.
UIDAI also introduced biometric locking, allowing individuals to lock and unlock their biometrics through the mAadhaar app. This ensures that biometric authentication cannot be misused without the user’s knowledge.
4. OTP and Multi-Factor Authentication (MFA)
Aadhaar authentication supports Multiple Authentication Types:
- Demographic authentication (name, date of birth)
- Biometric authentication
- One-Time Password (OTP) authentication
Read more about biometric Aadhaar authentication and its unique advantages.
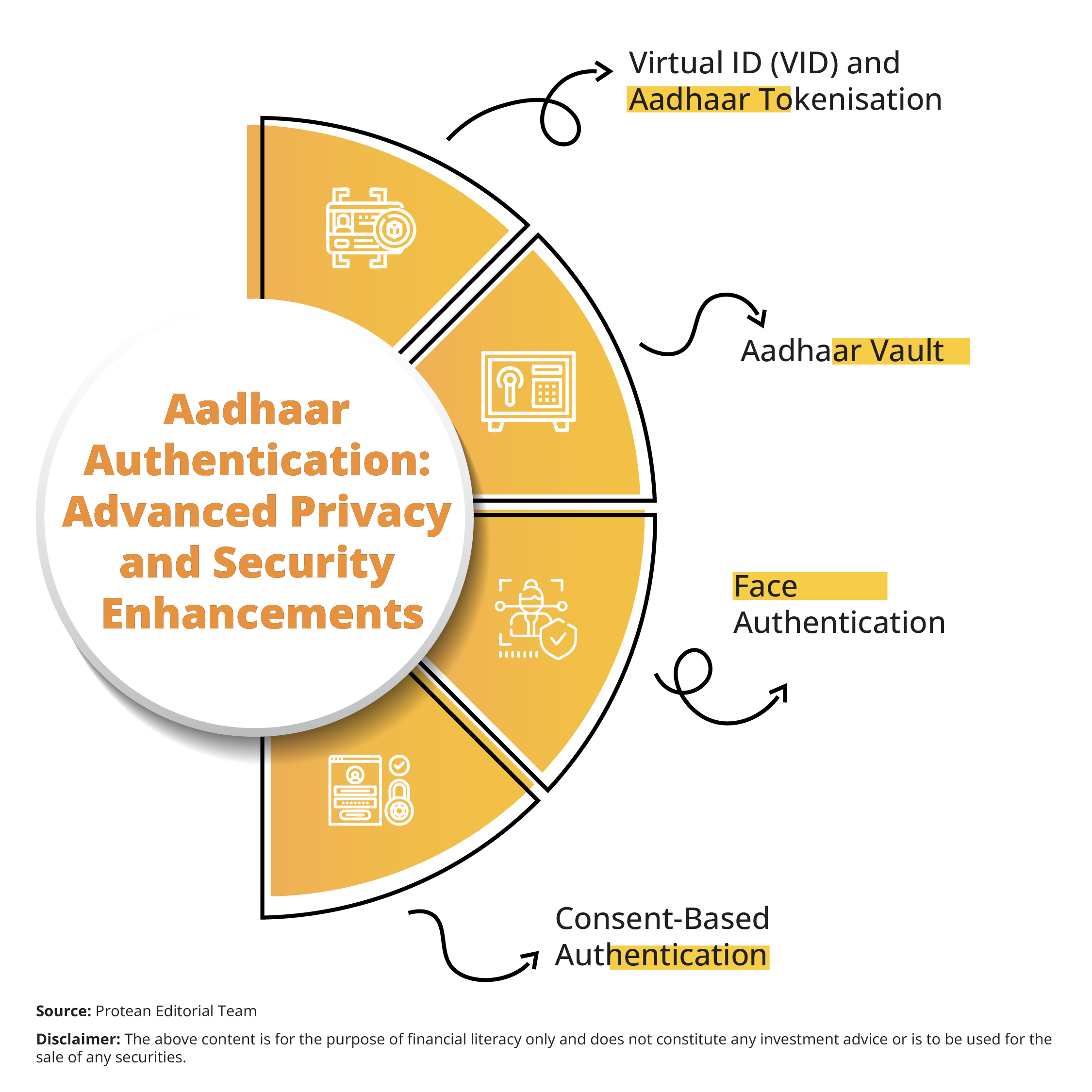
Advanced Privacy and Security Enhancements
UIDAI continues to evolve its security measures with innovations aligned to global best practices.
1. Virtual ID (VID) and Aadhaar Tokenisation
Introduced in 2018, the Virtual ID (VID) is a revocable, 16-digit pseudo-Aadhaar number that users can generate and use in place of the actual Aadhaar number for authentication. It reduces the risk of Aadhaar number exposure.
Alongside VID, UIDAI also allows for tokenised Aadhaar numbers for KYC purposes. These tokens are unique to each requesting entity and ensure that authentication history across services remains unlinked, thereby preserving user privacy.
2. Aadhaar Vault
To comply with data storage rules, regulated entities must store Aadhaar numbers in encrypted formats within Aadhaar Vaults. These are secure repositories audited by UIDAI. No unencrypted Aadhaar number can be stored beyond permissible limits, ensuring that agencies handle data responsibly.
3. Face Authentication
UIDAI introduced Face Authentication as an additional modality in 2018. This offers flexibility for users who may face challenges with fingerprints (like senior citizens or manual laborers). Face authentication uses liveness detection algorithms, adding another security layer and reducing the likelihood of spoofing.
4. Consent-Based Authentication
Aadhaar authentication is always consent-based. UIDAI’s guidelines mandate that the user must be informed about the purpose, nature of information collected, and the entity requesting authentication. This aligns with the DPDP Act, 2023, which enshrines informed consent, purpose limitation, and data minimisation as key principles of personal data governance.
UIDAI has also made it mandatory for all requesting entities to display the UIDAI consent screen, reaffirming the user’s right to transparency and control.
Read about how Aadhaar verification can simplify business processes.
Conclusion
To conclude, Aadhaar authentication is not only functionally vital, but it is structurally secure.
As India's digital economy scales, from UPI transactions crossing ₹25.14 lakh crore in May 2025 to e-governance platforms serving crores of citizens, the need for secure, scalable identity verification will only grow. Aadhaar, with continuous innovations like VID, Aadhaar Vaults, and face-based authentication, ensures that both security and user trust remain uncompromised.
For businesses integrating Aadhaar into their customer journeys, and for citizens engaging in daily digital interactions, understanding these measures provides not just reassurance, but a clear path to compliant and confident participation in the growing Indian digital economy.
Why wait? Contact Protean to integrate Aadhaar Authentication APIs into your platform now.